🔒 Security & Compliance on Bare Metal: Less Surface, More Control
“Isn’t bare metal less secure than managed cloud?”
Only if you design it like it’s 2005.
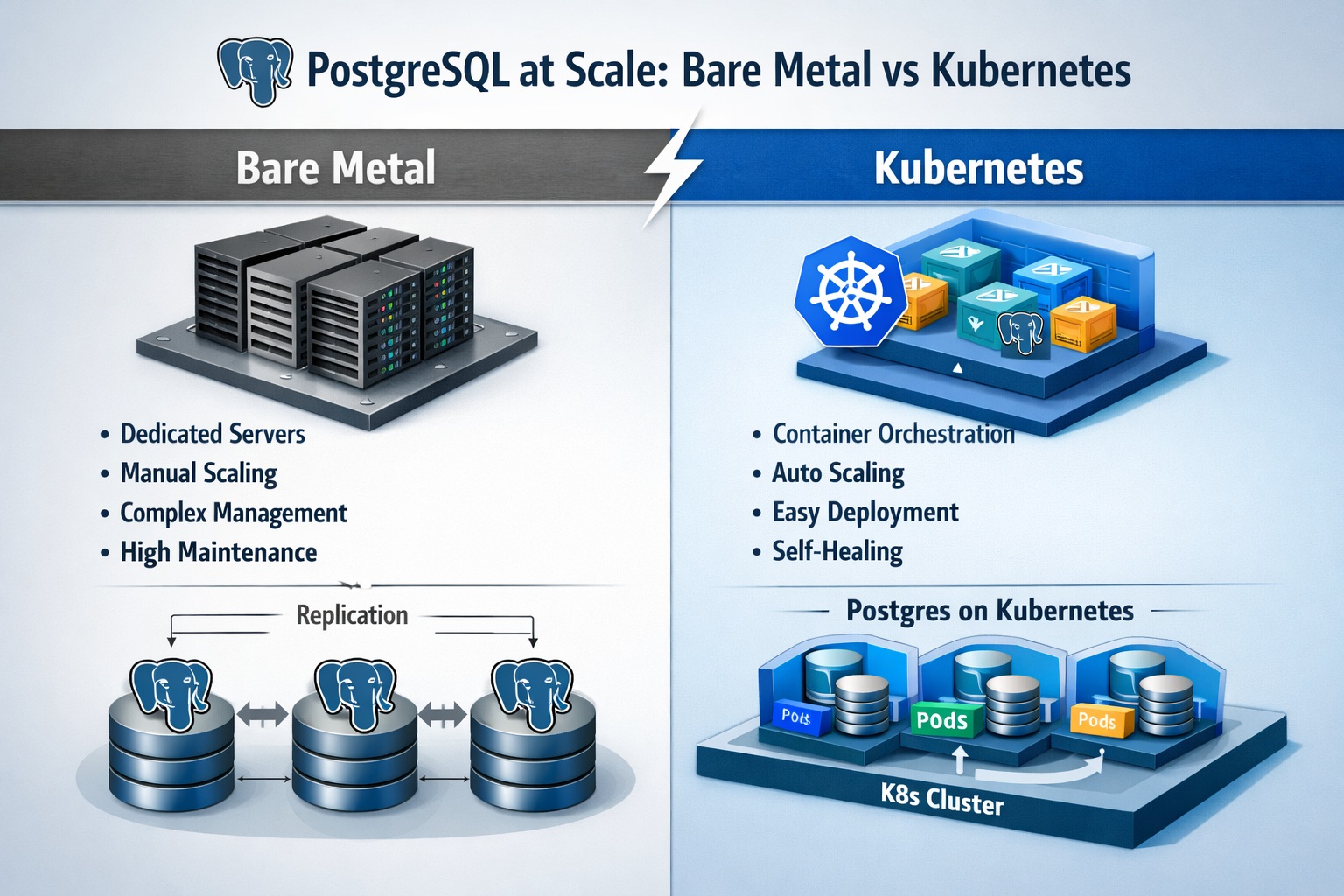
Modern bare metal in 2026 is not about SSH and snowflake servers. It’s about immutable provisioning, audit-ready change control, and zero-trust access—the same outcomes enterprise teams often expect when working with a kubernetes consultant for scale or a senior infrastructure leader.
When we migrated a mission-critical PostgreSQL environment off Kubernetes, we didn’t relax security—we tightened it by removing layers we could not fully observe, verify, or control end-to-end.
🔐 Our Production Security Model
| Layer | Implementation | Outcome |
|---|---|---|
| Provisioning | Immutable Ansible pipelines (no manual drift) | Reproducible builds, predictable state |
| Access Control | Zero SSH to production. All actions via Git → CI → Ansible | Full change history and approvals |
| Audit & Evidence | Change events shipped to SIEM + linked Confluence runbooks | Clear evidence for SOC 2 controls (change management) |
| Host Hardening | CIS-aligned hardening enforced via automation | Continuous compliance posture |
| Network Security | nftables + segmentation (DB subnet, app subnet, admin subnet) | Reduced blast radius, limited lateral movement |
| Secrets | HashiCorp Vault + short-lived credentials | No secrets in repos or manifests |
This approach is also the baseline we apply when delivering DevOps as a service for startups that need enterprise-grade controls without hiring a full in-house SRE team on day one.
🛡️ Why This Architecture Can Be More Secure Than Kubernetes by Default
Kubernetes is powerful, but the control plane and its ecosystem add operational and security surface area: kubelet, API server, etcd, admission controllers, CNI plugins, controllers—each requiring patching, hardening, policy enforcement, and continuous review.
By contrast, a hardened bare metal PostgreSQL HA setup often reduces moving parts and makes evidence collection simpler: fewer components to patch, fewer privileged paths, clearer network boundaries, and more direct host-level observability.
Cloud block storage can also limit the ability to independently validate implementation details (encryption posture, access paths, and performance characteristics). With bare metal, teams can prove controls end-to-end and keep tight ownership of the data layer.
📜 The Documentation Contract: Compliance by Design
“If it’s not documented with a recovery runbook, it doesn’t exist.”
Every critical component includes:
- Data flow diagram
- Threat model (STRIDE)
- Incident response playbook
- Quarterly access review policy
This is not overhead—it’s risk reduction. It reduces onboarding time, shortens incidents, and makes audits predictable.
🧩 How We Help Teams Scale (US/EU)
If you’re scaling a regulated or latency-sensitive platform, you typically need one of three engagement paths:
- Hire a senior DevOps engineer (remote) to lead infrastructure hardening, CI/CD governance, and audit-ready operations.
- Engage a Kubernetes consultant for scale when your bottleneck is multi-cluster reliability, network policy, or cost control— while keeping the most latency-sensitive stateful tier outside the orchestrator.
- Bring in a PostgreSQL high availability expert to design Patroni/etcd, HAProxy routing, backup/restore strategy, and failure testing.
For early-stage teams, DevOps as a Service for startups can be the fastest way to get production-grade posture: reproducible infra, secure delivery pipelines, and audit-ready documentation—without building an entire platform team immediately.
FAQ
Is bare metal actually compliant for SOC 2?
Yes—compliance is about controls and evidence. Immutable automation, change approvals, SIEM logging, access reviews, and documented recovery procedures often produce clearer evidence on bare metal than ad-hoc cloud workflows.
Should we run PostgreSQL in Kubernetes at all?
It depends on your SLOs. For dev/test and moderate workloads, operators can work well. If your production SLOs require sub-10ms p99 latency, deterministic failover, and deep host observability, a dedicated stateful platform is often safer.
When should we hire a senior DevOps engineer remotely?
When you need a single accountable owner to design secure operating models, reduce incident risk, and establish repeatable delivery and audit practices— especially across US/EU teams and time zones.
What does a PostgreSQL high availability expert typically deliver?
HA design (Patroni/etcd), failure testing, backup/restore drills, replication strategy, performance tuning, and an incident-ready runbook set.